P876
Forrest C. Lamb and Barbara Hough
Presented at the Twenty-second Annual Esri User Conference,
San Diego, California, USA
June 8-12, 2002
Sponsored by Environmental Systems Research Institute
(Esri)
ABSTRACT
This paper will focus on the use of GIS to ensure that antiterrorism and force protection standards are incorporated into the planning, programming, and constructing our communities. The paper will more specifically focus on the subject of Antiterrorism and Force Protection which a subset of the broader topic of emergency management. Situational awareness is key to developing a successful planning strategy. Will discuss examples of how GIS can be used as a tool to display and evaluate the impact of standoff distances and exclusive zones in community planning, to illustrate this point.
INTRODUCTION
Homeland Security
The President�s most important job is to protect and defend the American people.

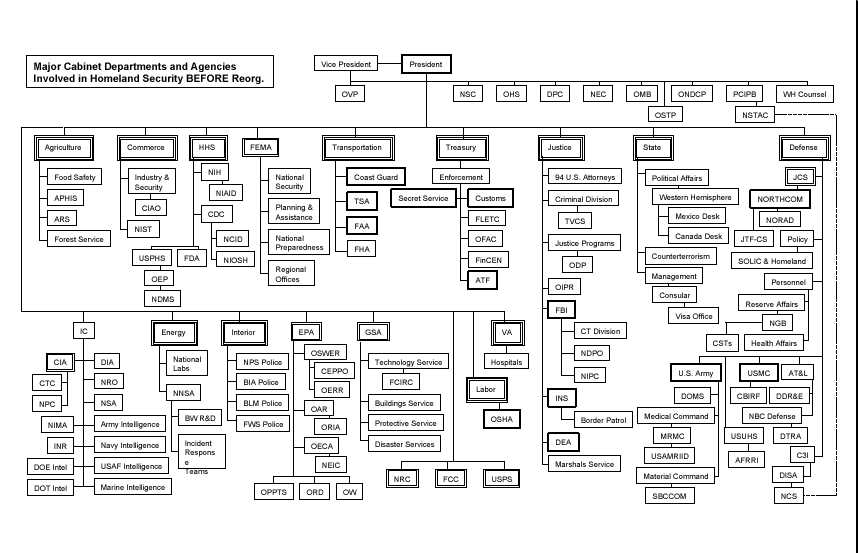
Figure 1. Major Cabinet Departments and Agencies Involed in Homeland Security Before Reorganization (Department of Homeland Security, President George W. Bush, June 2002 p. 10)
The changing nature of the threats facing America requires a new government structure to protect it against invisible enemies that can strike anytime with a variety of weapons. In fact, the responsibilities for homeland defense are currently dispersed among more than 100 different governmental organizations (See Figure 1). America needs a single, unified homeland security structure. In support of this concept, President Bush, in 2001, signed into being an Executive Order (EO) that established the Office of Homeland Security and the Homeland Security Council (See Figure 2). The EO contained the following:
Section 1. Establishment. I hereby establish within the Executive Office of the President an Office of Homeland Security (the "Office") to e headed by the Assistant to the President for Homeland Security.
Section 2. Mission. The mission of the Office shall be to develop and coordinate the implementation of a comprehensive national strategy to secure the United States from terrorist threats and attacks. The Office shall perform the functions necessary to carry out this mission, including the function specified in section 3 of this order.
Section 3. Functions. The function of the Office shall be to coordinate the executive branch�s efforts to detect, prepare for, prevent, protect against, respond to, and recover from terrorist attacks within the United States.
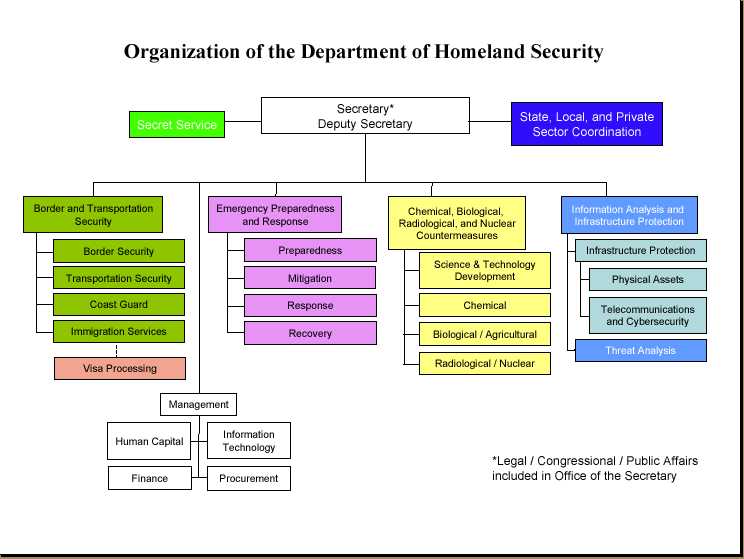
Figure 2. Organization of the Department of Homeland Security (Department of Homeland Security, President George W. Bush, June 2002 p.9)
MILITARY INSTALLATION FORCE PROTECTION PLANNING
Force Protection
Force protection is a phrase coined by the Department of Defense when discussing emergency management on its installations. Historically force protection, like telephones and computers, was considered as an afterthought and not as major component when planning facility or capital improvements. However, since September 11th, it has moved to the forefront in both the public as well as private sector. Force protection has become an integral part installation community planning.
Situational awareness is key to developing a successful force protection planning strategy. Will discuss how GIS can be used as a tool to display and evaluate the impact of standoff distances and exclusive zones in community planning to illustrate this point.
Assumption
There are no universal solutions to preclude terrorist attacks, since the threat is largely unpredictable and certainly will change over time�
Planners and designers must be innovative and alert to additional opportunities and techniques for integrating physical security measures into the design and planning of these facilities. Every design is a balance of competing demands and considerations such as building codes and regulations, aesthetic concerns, and budgets. In addition to these demands and considerations, antiterrorism measures should be consciously integrated into facility planning, design, and construction efforts.
The dynamic and opportunistic nature of terrorism hampers efforts to define the character and level of threat. The Air Force objective as prescribed by AFI 31-210, The Air Force Antiterrorism (AT) Program, "is to reduce the vulnerability of personnel and facilities to terrorism while balancing defensive measures with mission requirements and available resources." (Installation Force Protection Guide, p. 4)
"No matter how many measures are implemented risk is always present" (Structural Engineering Guidelines for New Embassy Office Buildings, U.S. Department of State Bureau of Diplomatic Security).
FORCE PROTECTION PLANNING (Installation Force Protection Guide, p. 3)
Force protection planning is a specific type of military planning. These studies are designed to protect resources: people, facilities, and equipment. It is accomplished through the planned and integrated application of principles such as antiterrorism and counter-terrorism and physical security (See Figures 3 and 4). These steps are described in the text that follows.
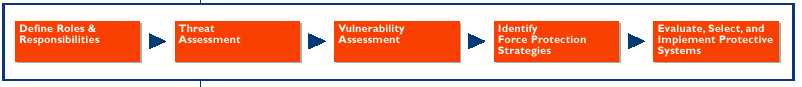
Figure 3. Force Protection Plan Development Overview (Installation Force Protection Guide, Fiure 2.1, p. 3)
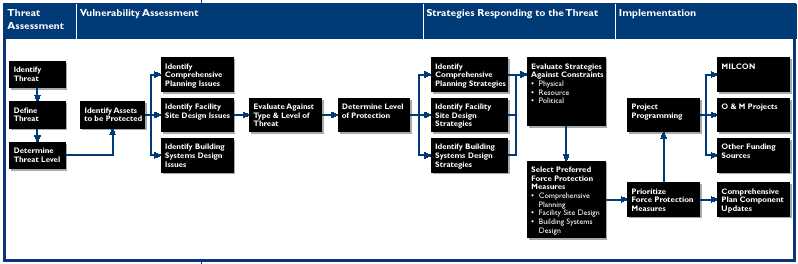
Figure 4. Force Protection Planning Steps (Installation Force Protection Guide, Figure 2.2, p. 3)
MILITARY INSTALLATION FORCE PROTECTION PLANNING
The installation planners, since the declaration of war on terrorism, are now looking for more than verifying spatial geometry or relationship of geographic features. Computer Aided Drafting can provide this service quite well. Planners now want to have the ability to link data sets together by geography and facilitate interdepartmental information sharing and communication. Much of the non-spatial data is already being stored in organizational databases. All that is left is to link it to the geography. One department or agency can benefit from the work of another by creating a shared database. This means that data can be collected once and used many times; reducing redundancy. This would facilitate the DoD in achieving the President�s goal of tearing down unwarranted information "stovepipes" and sharing homeland security information with relevant agencies.
"The President believes that an effective use of intelligence and closer coordination across all levels of government will help stop future terrorist attacks. In the wake of September 11, for example, we discovered that information on the hijackers' activities was available through a variety of databases at the Federal, State, and local government levels as well as within the private sector. Looking forward, we must build a system that combines threat information and then transmits it as needed to all relevant law enforcement and public safety officials." (President George W. Bush,"Using21st Century Technology to Defend the Homeland", Securing the Homeland Strengthening the Nation, The White House 2001, p. 19)
Military master planning has changed a great deal due to a renewed emphasis on compliance with Anti-Terrorism Force Protection (AT/FP) standards. When generating or updating plans it is more critical than ever to ensure that baseline data is accurate to provide situational awareness. Site visits to interview organizations and coordinate with the local community have always been standard. However, these visits now go beyond obtaining background information on mission and issues such as airfield encroachment, but also serve to uncover critical information regarding threat potential. Rather than simply verifying spatial data of the installation infrastructure, this data is now evaluated for violations and deficiencies. An opening in the perimeter security fence is an example of a deficiency that could be discovered during a field visit. Once this data has been gathered and updated into a database, Geographic Information System (GIS) becomes extremely helpful in the visualizing that which is necessary to develop a Force Protection Plan. GIS is even more helpful to envision the many force protection opportunities and constraints that affect the placement of structures such as buildings, towers, barriers, parking areas, etc. These restrictions rely on the calculations of standoff (buffers in GIS). For example, Quantity Distance (QD) arcs are buffers that are generated around facilities that contain High explosive munitions or flammable elements. The size and shape of these arcs depend on the type of facility and net explosive weight of the munitions being housed. There can be several buffers nested within each other and their size can dictate what kinds of facilities approved to be within a specified distance of the explosive. This analysis is as important as it is complicated. GIS can automate this process to ensure the arcs are properly generated and those facilities in violation are clearly identified.
This technology can be similarly applied to the airfield imaginary surfaces and force protection setbacks. It would be impossible to update all military installations to be in complete compliance with all force protection standards. However, it is possible and necessary to use GIS when planning to identify vulnerability and correct it when possible. GIS can be used in long range planing to communicate methods bring poorly placed facilities into compliance. Plans for development of new facilities should take an approach that considers a campus design with parking located a safe distance from buildings. GIS is a natural complement to military planning by providing a simple way to attain situational awareness, view disparate data types with common geography, and conduct analysis such as buffering with ease. The figure below illustrates these principles (See Figure 5).
Military installations will always manage explosive and hazardous materials to accomplish their unique missions. A typical installation has QD arcs to track munitions storage, liquid oxygen storage tanks, and segregated magazine areas. Propane fuel tanks for fire training can be especially hazardous. These QD arcs often encroach upon the neighboring community. Parking lots that are AT/FP Non-Compliant are either too close to an occupied facility or are within the QD arc. Buildings that are non-compliant may be too close to the perimeter, a parking lot or within a QD arc.
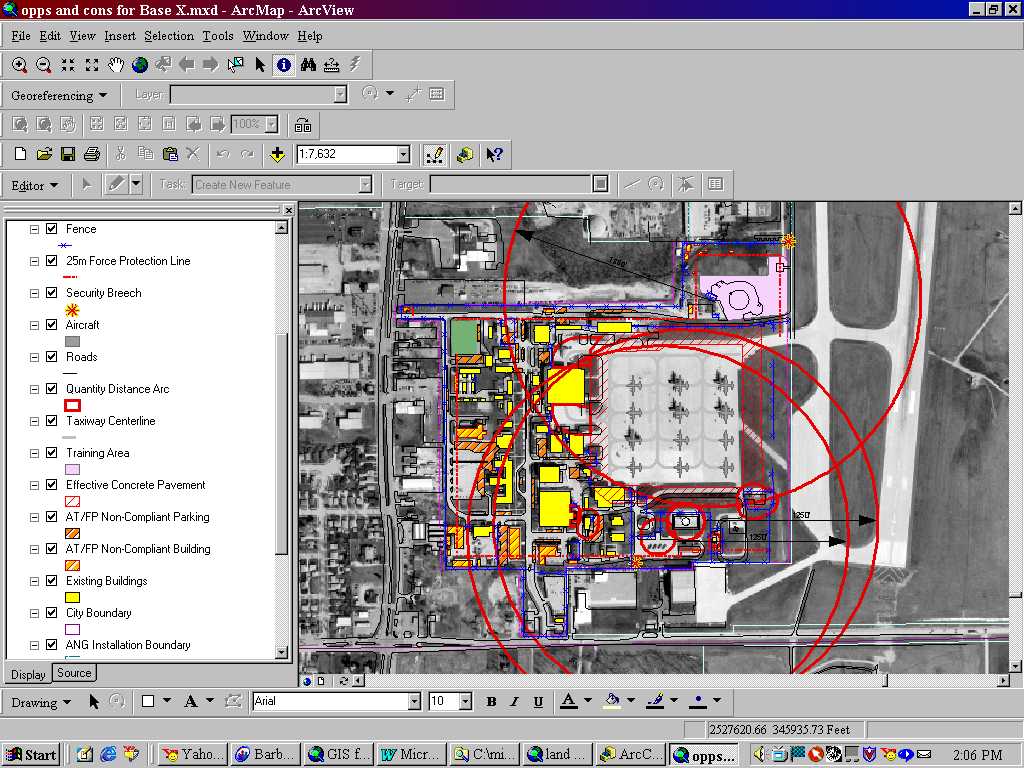
Figure 5. Base "X" Force Protection Plan
SUMMARY
There are no universal solutions to preclude terrorist attacks, since the threat is largely unpredictable and certainly will change over time�
Planners and designers must be innovative and alert to additional opportunities and techniques for integrating physical security measures into the design and planning of these facilities. Every design is a balance of competing demands and considerations such as building codes and regulations, aesthetic concerns, and budgets. In addition to these demands and considerations, antiterrorism measures should be consciously integrated into facility planning, design, and construction efforts. (Installation Force Protection Guide, p. 4)
GIS technology can facilitate tearing down unwarranted information "stovepipes" and make it more easier to share homeland security information with required Federal, State, local and relevant private sector agencies. Maps are 2-dimensional representations of our real world. GIS makes it possible to manipulate large amounts of geospatially referenced data and convert it into information. It�s become an integral part of the planning process.
GLOSSARY (Installation Force Protection Guide, p 39 - 40)
Antiterrorism Defensive measures used to reduce the vulnerability of individuals and property to terrorist acts, to include limited response and containment by local military forces.
Antiterrorism Awareness Fundamental knowledge of the terrorist threat and measures to reduce personal vulnerability to terrorism. See also antiterrorism.
Area Commander A Military Service-designated commander with authority in a specific geographical area.
Area of Responsibility The geographical area associated with a combatant command within which a combatant commander has authority to plan and conduct operations. Also called AOR.
Asset Any potential target of terrorist attack, most commonly people, equipment, a building, or an outdoor venue (in whole or in part).
Blast Curtains Heavy curtains made of blast resistant materials that could protect the occupants of a room from flying debris.
Blast Vulnerability Envelop The resources around an explosive device that will be damaged by the blast.
Clear Zone An area that is clear of visual obstructions and landscape materials that could conceal a threat or perpetrator.
Commander Any commanding officer, installation commander, or other appropriate command authority, or civilian supervisor in a comparable position.
Counterintelligence Information gathered and activities conducted to protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations, or persons; or international terrorist activities, excluding personnel, physical, document, and communications security programs.
Counterterrorism (CT) Offensive measures taken to prevent, deter, and respond to terrorism.
Domestic Terrorism Terrorism perpetrated by the citizens of one country against fellow countrymen. That includes acts against citizens of a second country when they are in the host country, and not the principal or intended target.
Ductile Materials Materials that are malleable and will absorb impact loads without breaking.
Electronic Security Systems (ESS) That part of physical security concerned with the safeguarding of personnel and property by use of electronic systems. These systems include, but are not limited to, intrusion detection systems (IDS), automated entry control systems (AECS), and video assessment systems.
Exclusive Zone An area around an asset which has controlled entry with highly restrictive access.
Force Protection Security program designed to protect Air Force personnel, civilian employees, family members, facilities, and equipment, in all locations and situations, accomplished through planned and integrated application of combating terrorism, physical security, operations security, personal protective services, and supported by intelligence, counterintelligence, and other security programs.
High-Risk Target Any U.S. material resource or facility that, because of mission sensitivity, ease of access, isolation, and symbolic value, may be an especially attractive or accessible terrorist target.
Installations Air Force including bases, stations, and annexes (both contractor and Government operated), hospitals, terminals, and other special mission facilities, as well as those used primarily for military purposes. Also includes any activity of the Air Force that employs members of the work force in peacetime or will employ them in the event of mobilization.
Internal Damping Anything that absorbs some or all of the impact from a blast.
Military Facility A facility subject to the custody, jurisdiction, or administration of any DoD Component. This term includes, but is not limited to, military reservations, installations, bases, posts, camps, stations, arsenals, or laboratories where a DoD Component has operational responsibility and has responsibility for facility security and defense.
Non-Exclusive Zone An area around an asset that has controlled entry but less restrictive access than a exclusive zone.
Nuclear, Biological or Chemical Weapons (NBC) Also called Weapons of Mass Destruction (WMD). Weapons that are characterized by their capability to produce mass casualties.
Physical Security The part of security concerned with measures/concepts designed to safeguard personnel; to prevent unauthorized access to equipment, installations, materiel, and documents; and to safeguard them against espionage, sabotage, damage, and theft.
Sacrificial Roof or Wall Walls or roofs that can be lost in a blast without damage to the primary asset.
Safe Haven Secure areas within the interior of the facility. A Safe Haven should be designed such that it requires more time to penetrate by terrorist than it takes for the response force to reach the protected area to rescue the occupants.
Stand-off Weapons Weapons that are launched from a distance at a target (anti-tank weapons, mortars, etc.).
Stand-off Distance The distance between an asset and a threat.
Terrorism 1. The calculated use of violence or threat of violence to inculcate fear; intended to coerce or to intimidate governments or societies in the pursuit of goals that are generally political, religious, or ideological. 2. The unlawful use or threatened use of force or violence against individuals or property to coerce or intimidate governments or societies, often to achieve political, religious, or ideological objectives.
Threat Analysis In antiterrorism, threat analysis is a continual process of compiling and examining all available information concerning potential terrorist activities by terrorist groups that could target a facility. A threat analysis will review the factors of a terrorist group�s existence, capability, intentions, history, and targeting, as well as the security environment within which friendly forces operate. Threat analysis is an essential step in identifying probability of terrorist attack and results in a threat assessment. See also antiterrorism.
Vulnerability 1. The susceptibility of a nation or military force to any action by any means through which its war potential or combat effectiveness may be reduced or its will to fight diminished. 2. The characteristics of a system which cause it to suffer a definite degradation (incapability to perform the designated mission) as a result of having been subjected to a certain level of effects in an unnatural (man-made) hostile environment.
BIBLIOGRAPHY
FEDERAL GUIDANCE
DEPARTMENT OF DEFENSE GUIDANCE
AIR FORCE GUIDANCE
Publications
Authors
Forrest C. Lamb
926th FW/CE, Base Civil Engineer
400 Russell Ave
NAS JRB New Orleans, LA 70143
Comm: (504) 678-3735
forrest.lamb@neworlearns.af.mil
Barbara Hough
GIS Project Manager, URS Corporation
9960 Federal Ave. Suite 300
Colorado Spring, CO 80921
Barbara_hough@urscorp.com