The Department of Public Works for the City of Houston, Texas has undertaken a major GIS Data Conversion and Applications project titled the GIMS Project. As part of this effort, the Graphics and Engineering Management Branch must audit and accept the converted data. They also need to perform initial data edits and long term data updates utilizing a city wide network with DEC/OSF1 v.3 running on an Alpha System and customized GIS software. To accommodate these tasks an extensive database security system has been developed which enables separate privileges for viewing and editing of data, utilizing user group classifications which are divided by privileges, and a Work Flow Model to be performed on an expansive hardware and software network configuration.
The configuration calls for five levels of database security. The first level of security is for the Database Administrator and requires write access to the data and the ability to copy data from working to permanent storage. The second level is for the Supervisors who will assign data to editors from the working library to the local workstation and copy the updated data to the preliminary permanent storage library. The third level involves the Editors who require write access to update the data which is contained on the Editors local workstation. The fourth level is for auditing data in a read only mode. The final level is the Database Operator who has only the privilege to load the data from 4mm tape onto the system.
Additionally, there are three ArcInfo map libraries and twelve workstations each with local data storage capacity with different levels of security. There are four remote user sites with plans to add at least one more, each with local graphical data storage in a map library. In the customized editing software program, Editors have exclusive write access to one map for updates while the auditors can have read access to the same data if necessary. The editors also have read access to any neighboring data as required. The purpose of this paper will be to examine more closely how multiple levels of database security have been provided for a comprehensive and expansive GIS through work flow models, access privileges, hardware and software configurations.
The Department of Public Works and Engineering (DPW&E) of the City of Houston, Texas has undertaken one of the nation's largest GIS Data Conversion and Applications projects for Utility Data Management. This multi-million dollar project is titled the Geographic Information Management System (GIMS). This project involves many different areas of data management. Some of these areas include data auditing, editing and maintenance, applications, statistical analysis, remote site data operations, and multiple site data output. As the project manager for GIMS, RJN Group, Inc., is responsible for integrating the various aspects of this project and delivering a complete, turn-key system to the City of Houston (COH). One of the challenges in this project was developing a comprehensive and beneficial security system. Through a series of in-depth meetings and feedback from the COH, a security system design document was custom developed. The GIMS Database Security System design has six main components. These are hardware setup, software setup, user classification, data work flow, applications, and system administration responsibilities. This paper will explore in detail, the solution for the GIMS Project concerned with data Auditing and Editing at the Map Maintenance site and the security measures involved with the distribution of updated data.
The hardware configuration for the GIMS project varies by location. In addition to a central Map Maintenance site, there are several Remote site locations. These remote site locations access the database for the purpose of performing mostly unscheduled and some scheduled maintenance. With automated access to a digital database, their work in locating and gathering information on a specific facility is greatly simplified. Users at these sites have read only access to the data. Only the Map Maintenance site has the privilege to make changes to any part of the database.
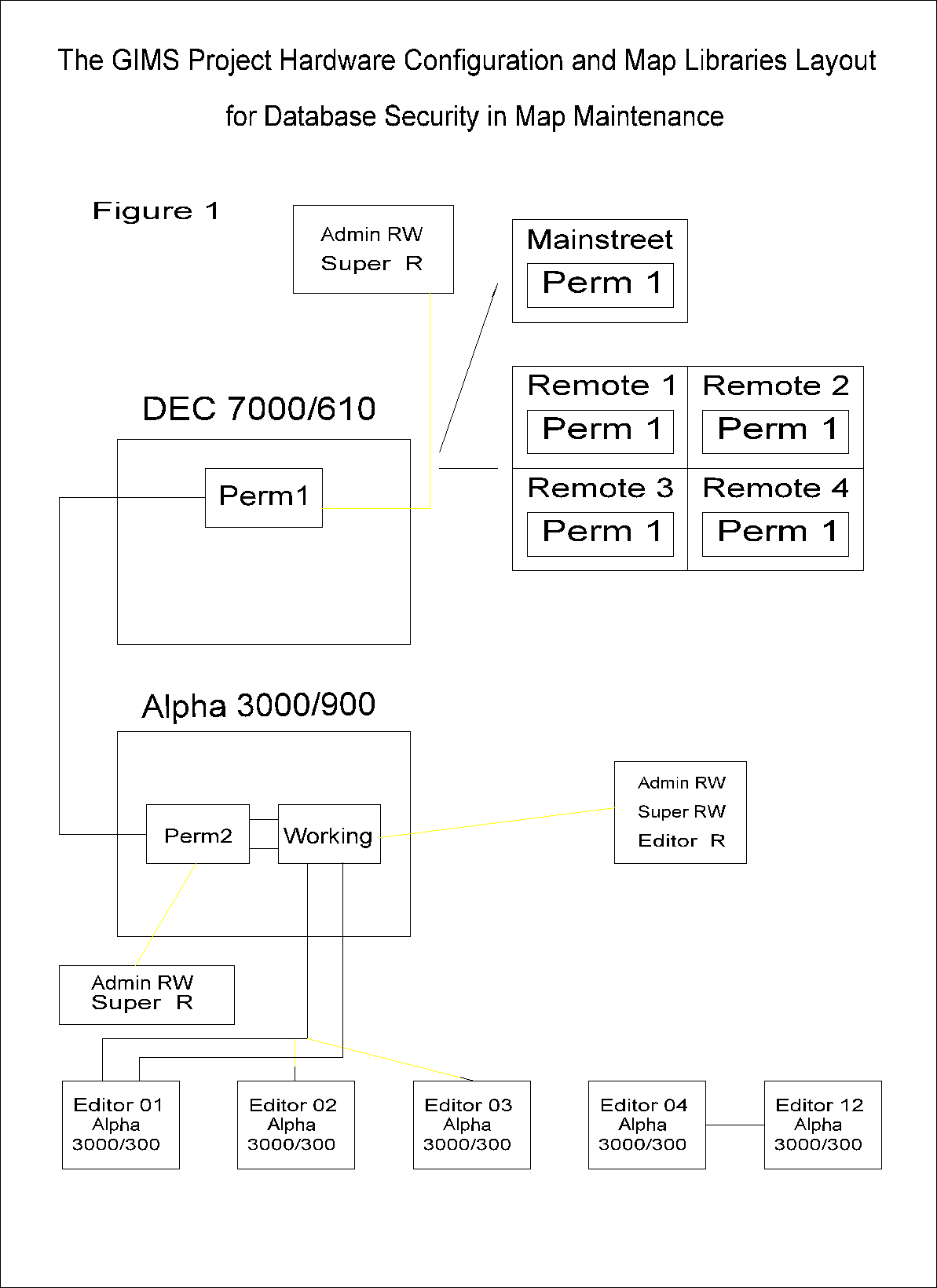
Currently there are four remote sites, one is located in each quadrant of the City of Houston. These sites are identified as Northeast Quadrant, Northwest Quadrant, Southwest Quadrant, and Southeast Quadrant. Hardware configuration for these sites locations consist of an Alpha 3000/800 server and three Digital Equipment Corporation (DEC) VXT2000+ x-terminals which operate directly from the server. Additionally these sites each have a thermal or laserjet plotter and a printer for output.
There is also an additional site located on Main Street which will also have a connection into the GIMS database. At this site users will be able to view the data and use the same applications as described above for the quadrants. This site would consist of an Alpha 3000/300 workstation which would access the database and run its applications locally. The Main Street location would also have a plotter and printer for output.
The central site for the GIMS Project is the Map Maintenance location where all data updates are done and distributed to the remote sites. This is where the System Administrator would reside and be responsible for the integrity of the entire database. The hardware configuration for this location consists of a DEC 7000/610 server, an Alpha 3000/900 server, a DEC VXT2000+ x-terminal for system administration activities, several DEC VLC 2000 workstations, and twelve Alpha 3000/300 workstations for editing activities. Additionally there is an electrostatic plotter and several printers for data output.
All four city quadrants and Main street are connected through a Wide Area Network (WAN) to the Map Maintenance site.
The GIMS Project software solution is based on an OSF1/ v.3 operating system and utilizes ArcInfo based tools such as Map Librarian, ARC/EDIT and ARC/PLOT for its graphical applications and a CASS WORKS solution for the attribute applications and data storage. Attribute information refers to the information which is tied to the graphic elements of a map such as the size or material of a water main.
Each of the Remote Quadrant sites are configured identically. Each server holds a map library containing the database for the entire City of Houston. The x-terminals access the server and run the application programs which are in view only mode.
The Mainstreet location will also have a map library which will contain the entire database and will run the same view only application programs locally.
Each Remote site location will access the attribute information across the WAN from the Map Maintenance site DEC 7000/610 library. The graphical information will be accessed from the local map library.
The Map Maintenance site houses a total of three map libraries. The master copy of the database will reside on the 7000/610 server and is identified as PERM1. Updated data is distributed from this library to all of the Remote sites daily. There also exists an identical backup copy of the PERM1 library called PERM2. Data is downloaded from the PERM2 library into a library called WORKING on the 3000/900 server to be distributed to the Editors for updates. This is also where the data is checked for work quality after edits have been performed before the data is returned to permanent storage. In addition to the map libraries, there is an exported disk partition shared by the 3000/900 server and all of the 3000/300 workstations which will facilitate the most efficient export of data from the WORKING map library to the local workstation.
Please refer to figure 1.a for a more detailed description of both the hardware and software configurations for the GIMS System.
The user access levels are an important part of the security system design. They control who has the ability to make changes to the database, the application programs, the passwords, the user accounts, and more. For the Map Maintenance site, there are several user access levels to provide optimal utilization of the system for the purpose of auditing and editing the data. Each user has an individual login on the system. Each login is assigned to a user group. These user groups are listed and described below.
The System Administrator is the highest privileged group and is assigned superuser privileges. Only one or two people will be assigned to this group at any one time. This user must be responsible for the maintenance of the system and the integrity of the data. The System Administrator will control user accounts. Modifications for staff changes are easily made by assigning a higher or lower level classification to a user. The System Administrator also has special privileges for the map libraries. Full map library privileges, including read and write, are given to this user for carrying out the exclusive responsibility of loading the updated data into the PERM1 library and distributing it to the Remote sites.
The Supervisor level has read and write privileges to the PERM2 and WORKING libraries as well as the 3000/300 workstations, and read only privilege to the PERM1 library. The Supervisor plays a key role in controlling the movement of data through the Work Flow process for performing updates. The Supervisor is responsible for assigning data to the Editors for work and copying the map to the local workstations. This user is also responsible for auditing the work of the Editor to ensure the integrity of the database. Once the work of the Editor has been approved by the Supervisor, this user must then return the data to the PERM2 library.
The Editor has read and write privileges only to the local workstations. This user is given an individual account and is responsible for making all updates and changes to the database using customized software application programs. A log file keeps track of all the changes made to the data during an edit session. This user cannot access any edit tools which are on the system or utilize the OSF1 rcp command (remote copy) which would allow data to be copied across the network. Editors' work is localized on the workstation.
This user group is similar to the Editor group except that all aspects of this account are read only. The Auditor will utilize highly customized software application programs to review the data to ensure its quality. Members of this group are not provided with any tools which would allow changes to be made to the data, system or application files, or copy anything across the network. The Auditor is localized to the workstation and not allowed to make changes even there.
The Remote Viewer accounts belong to a user group with read only privileges on the Remote system to which they belong. For example, a user in the Northeast Quadrant would be assigned a Remote Viewer account on that system. The restrictions applied to these accounts are the same as that for the Auditor group at the Map Maintenance site. These accounts are assigned to the end user, those running the applications at the Remote sites.
This user group has the lowest privilege of all the user groups. The role of the Database Operator is to load any data on the 3000/900 server which is delivered on 4mm tape into the system to a particular directory. The write privileges of this user are restricted to the directory into which data is to be loaded. The System Administrator is then responsible for installing the data into the map libraries. Under the supervision of the System Administrator, this user may also run preset, automated programs to perform nightly system backups but would not be responsible for restoring data to the system.
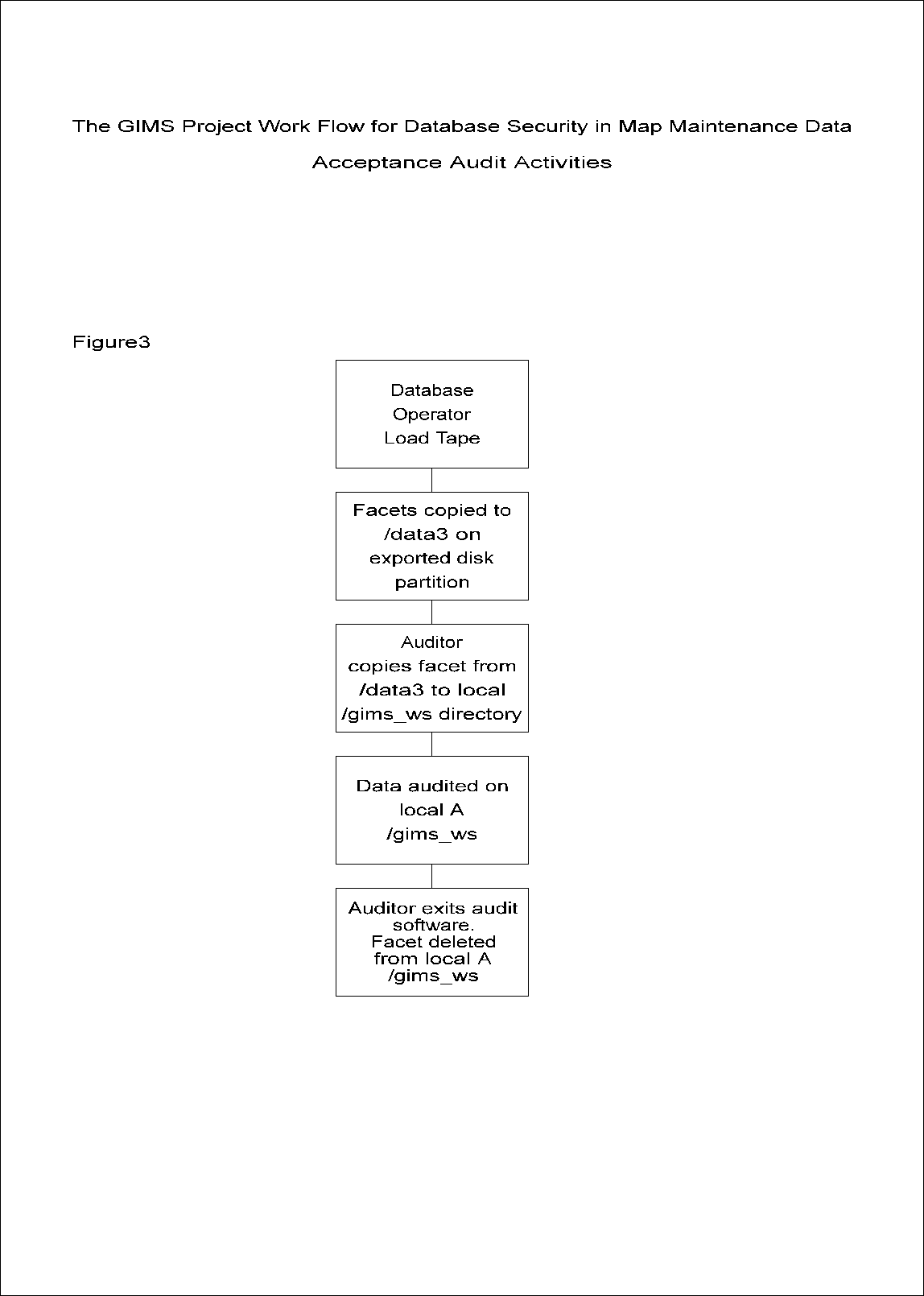
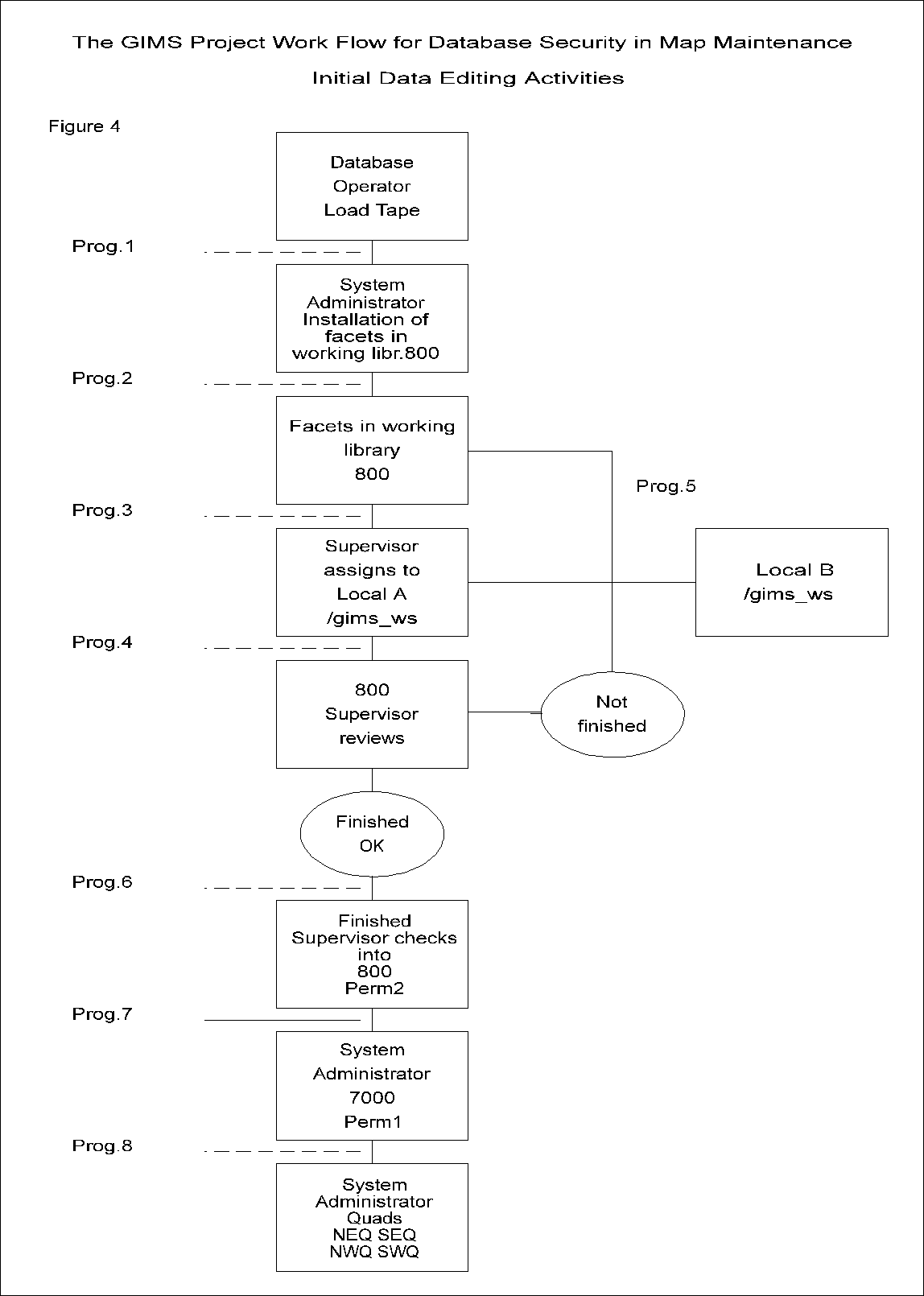
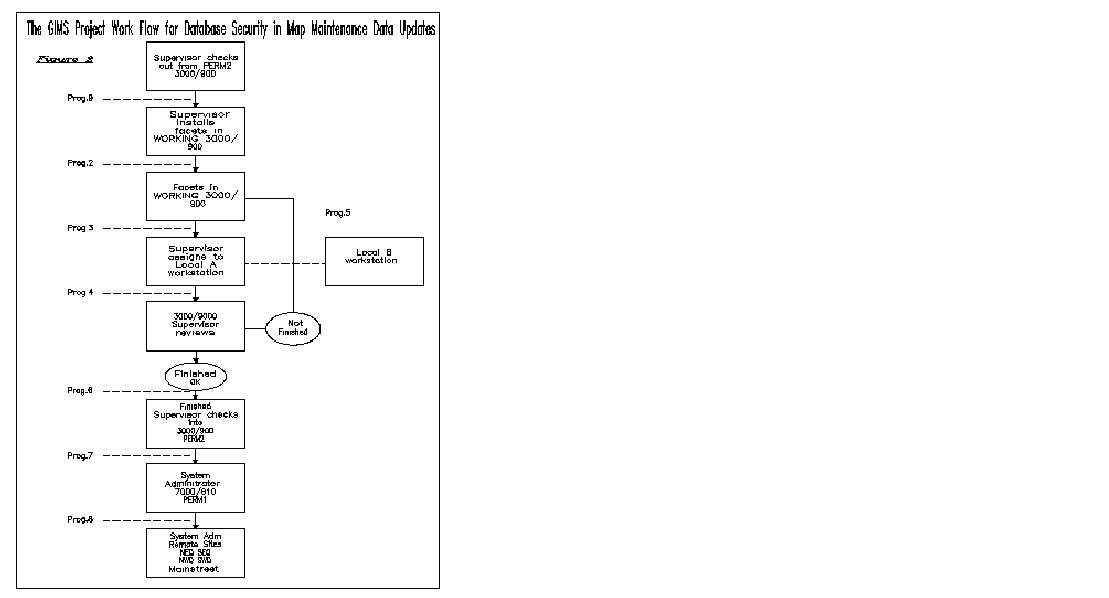
When maintaining over 2,500 map tiles movement of data across a city wide network must be carefully managed. When changes to the data are required, there is a need to restrict certain access to the data. The Work Flow Model for the GIMS Project was designed specifically for the hardware and software configurations. The database security design for map maintenance carefully controls the flow of the updated data from the local workstation of the editor to the permanent storage map library PERM1. It is based on the user groups described above. Each user group has specific responsibilities in handling the data when editing is to be performed. Figure 2.a shows a diagram of the Work Flow Model for the GIMS system.
The Work Flow Model begins with the Supervisor checking out a map from the PERM2 library which is a duplicate of the PERM1 master library. The Supervisor then programmatically installs the map into the WORKING library on the same Alpha 3000/900 server. With the map in the WORKING library, a Supervisor will then assign the map to an Editor by running a program which will check the facet out of the WORKING library and copy it to a directory on a local Alpha 3000/300 workstation where the file ownership will be transferred automatically to the Editor.
The Editor then performs the changes to the map and signals to a Supervisor that the assignment is finished using the OSF/1 mail tool.
After receiving the mail message, the Supervisor utilizes a program to change the file ownership of the map to Supervisor and reinstalls it into the WORKING library. When it is convenient, the Supervisor then has the option to copy the map from the WORKING library to a local workstation, to review the work of the Editor and assess whether or not the assignment has been completed satisfactorily. If the edited map is approved then the Supervisor proceeds to the next step. However, if the assignment has not been completed satisfactorily or the Editor cannot continue to complete the assignment for any reason the Supervisor programmatically returns the map to the WORKING library. From here the Supervisor reassigns the map to either the same Editor or a different Editor. Once the changes to the map have been completed and approved by a Supervisor, the Supervisor then checks the map into the permanent storage library, PERM2 on the Alpha 3000/900 server, programmatically changing the file ownership to root. The Supervisor then uses the mail tool to signal the System Administrator that the map is approved and checked into the PERM2 library.
There are many steps required for security when addressing the complex issues involved with data editing. While the operating system customizations and the Work Flow Model programmatically relieve some of the security burdens involved with such changes, the Editor must be responsible and skilled. In an effort to minimize, as much as possible, the responsibility of the Editor concerning connectivity of the facility network, an extensive editing program was developed The GIMS Map Maintenance for Editing software is highly customized and has been designed with strict database security controls in place.
Editors require exclusive write access to one map for updates while others have read access to the same map if necessary. At the same time, the Editor must have read only access to all neighboring maps. The solution to both of these issues is that only the edited map which has been assigned to the Editor by the Supervisor is copied back to the WORKING library, the read only maps are deleted from the local workstation upon exiting the session.
Connectivity issues must be considered as well and monitored with every edit action taken. These issues can be divided by graphic and attribute information. The network connectivity must be maintained for both of these issues. To resolve this problem, appropriate controls in the applications software have been programmed to automatically stop the Editor from proceeding until the correct steps have been taken to maintain connectivity.
For example, when performing graphical edit actions such as adding a network line which would alter the connectivity of the line and its associated symbols, the user is prompted to follow up by adding the attribute information for the new line and updating any associated unique identifiers or symbols on the connecting lines. Additionally, lines and points are snapped automatically and the user is prompted for annotation additions if necessary.
Attribute information such as unique identification numbers which are maintained with each map element, are programmatically generated and regenerated as necessary in the editing tools. The user is not responsible for entering or maintaining the unique identification structure. Other attribute information controls are automated as well. For example, the system requires the user to automatically update annotation whenever attribute information has changed. Additionally, the programs automatically prompt the user for associated attribute information corrections to follow all graphic changes to map features. For example, if a new valve is added, the user is not permitted to continue in the program until the attribute information for the new valve has been provided. Such programming controls help to maintain the consistency and integrity of the database and are an absolute necessity when dealing with such an enormous database.
A customized user log file is automatically generated with every Edit session. This log file contains such information as edit actions executed, user name, date and time. This log file remains with the map data while it is in the Work Flow process, then it is archived and kept by the System Administrator. While the map is in the process of being edited, the Supervisors can check all actions taken by an Editor if necessary. Since the log files are hidden, and the Editor user group has no access to system editing tools the files are safe from any changes being made to them. Additionally, the 3000/300 workstations have no devices configured on them so the Editor could not use a tape drive or other device to load and replace a different log file for a map on the system. If a map comes to a Supervisor without a log file, the Supervisor is immediately aware that something is not right with that map and has the option to either order an audit to be performed on the data or delete that particular map and restart the edit process.
There are certain measures which can only be managed by a System Administrator who has the superuser privilege and is authorized to take responsibility for the protection of the system. The GIMS system is no exception to this concept. Some of the key system security responsibilities of the Systems Administrator are described below.
As described in detail above, the System Administrator has a fundamental role in the Work Flow Model. Only one or two members of this group have exclusive authority to move updated data from the PERM2 library to the PERM1 master library. The System Administrator is also responsible for distributing the final data from the PERM1 master library to the Remote site libraries as the final step in the Work Flow Model. Without the fulfillment of these responsibilities, the quality control measures and distribution of updated data could not be strictly regulated.
Losing data on any system is a problem and can be a nuisance. Losing data on a system as complex as the GIMS system is simply unacceptable. Therefore a plan for system backups has been developed. The System Administrator is ultimately responsible for ensuring that these backups are performed by the Database Operators. Programs are provided for daily data backups for both servers at the Map Maintenance site. Additionally, remote data backups are performed of all 3000/300 and 3000/200 workstations on a daily basis to limit the risk of updated data loss to less than one day in the event of an emergency. Weekly data backups are recommended for the Remote site systems since they are identical copies of the PERM1 master library and could be restored from there if necessary. Programs which perform both local and remote operating system level backups should be run at least on a monthly basis by the System Administrator. Following this prescribed method of backing up the database and the system will provide insurance against an unrecoverable crisis.
In addition to participating in the flow of the data through the update process and performing system backups, the System Administrator is responsible for managing the user accounts. Such tasks as adding new users, upgrading or downgrading a users group privileges, removing user accounts, and overwriting user passwords when necessary will be the responsibility of the System Administrator of the GIMS system. Since the Audit and Edit group users of this system are mostly inexperienced with operating system level applications and procedures these users will not be responsible for managing their own accounts. User accounts will have to be periodically cleaned by the System Administrator under the superuser privilege for such items as temporary files.
Two of the more obvious concerns of securing any computer system are blackouts and power surges. In the event of a power failure, an Uninterruptable Power Supply (UPS) unit will keep the system running for a finite period of time, thereby allowing the System Administrator to shut down the system in the appropriate manner. An available feature of the UPS units which may be provided for the GIMS system is a page feature which will automatically notify the System Administrator as soon as a power failure occurs. If the System Administrator is unable to take advantage of the additional time and the system does go down on its own, the UPS unit will absorb power surges which may occur when power is restored. Plans for the GIMS system UPS unit implementation are as follows.
The 7000/610 server will have an attached UPS unit which will keep the system running for forty to forty-five minutes after the power goes out. The 3000/900 server will have a similar system to keep it running for thirty minutes after a power failure. This will allow the System Administrator additional time after a power failure to halt processes and shutdown the machines in the most safe and efficient manner. The 3000/300 and 3000/200 workstations will not be provided with UPS units.
Remote site servers will be provided with UPS units which will allow thirty minutes for the System Administrator at the Map Maintenance site to login on the network and order a remote shutdown of that system.
The six primary concepts of the GIMS Database Security System as described above are hardware setup, software setup, user group classifications, data work flow, applications, and system administration responsibilities. This system has been designed with one primary focus and that is data integrity. The Work Flow Model dictates accountability by user for the integrity of the data in the form of data possession and log files. In addition to the security of the database, system configurations are also protected in crisis situations and power failures. An extensive backup procedure will allow for partial or complete restoration of any part of this system if necessary.
These database security measures for the GIMS Project are comprehensive and facilitate the management of a large database with remote site layouts. The security measures described in this document allow the Department of Public Works and Engineering to control the access to their system and database for either map maintenance activities or running applications. Having confidence in their database allows the management of DPW&E to concentrate their efforts on effectively managing their infrastructure system.
He, Henry
Programmer Analyst, RJN Group, Inc.
1003 Wirt Rd. Suite 204
Houston, TX 77055
Telephone: (713) 465-4474
FAX: (713) 465-4490
Morgan, Lisa R.
Programming Coordinator, RJN Group, Inc.
1003 Wirt Rd. Suite 204
Houston, TX 77055
Telephone: (713) 525-9910
FAX: (713) 465-4490